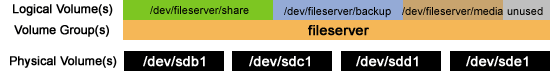
In this chapter we will learn how to resize our logical volume
share
which has an ext3 filesystem. (I will show how to resize logical
volumes with xfs and reiserfs filesystems further down this tutorial.)
First we must unmount it:
kilo:~# umount /var/share
kilo:~# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/sda2 19G 665M 17G 4% /
tmpfs 78M 0 78M 0% /lib/init/rw
udev 10M 88K 10M 1% /dev
tmpfs 78M 0 78M 0% /dev/shm
/dev/sda1 137M 17M 114M 13% /boot
/dev/mapper/fileserver-backup
5.0G 144K 5.0G 1% /var/backup
/dev/mapper/fileserver-media
1.0G 33M 992M 4% /var/media
Now let's enlarge
share from 40GB to 50GB:
kilo:~# lvextend -L+50G /dev/fileserver/share
Extending logical volume share to 50.00 GB
Logical volume share successfully resized
Until now we have enlarged only
share, but not the ext3 filesystem on
share. This is what we do now:
kilo:~# e2fsck -f /dev/fileserver/share
e2fsck 1.40-WIP (14-Nov-2006)
Pass 1: Checking inodes, blocks, and sizes
Pass 2: Checking directory structure
Pass 3: Checking directory connectivity
Pass 4: Checking reference counts
Pass 5: Checking group summary information
/dev/fileserver/share: 11/5242880 files (9.1% non-contiguous), 209588/10485760 blocks
Make a note of the total amount of blocks (
10485760) because we need it when we shrink
share later on.
kilo:~# resize2fs /dev/fileserver/share
resize2fs 1.40-WIP (14-Nov-2006)
Resizing the filesystem on /dev/fileserver/share to 13107200 (4k) blocks.
The filesystem on /dev/fileserver/share is now 13107200 blocks long.
Let's mount
share:
kilo:~# mount /dev/fileserver/share /var/share
kilo:~# ~# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/sda2 19G 665M 17G 4% /
tmpfs 78M 0 78M 0% /lib/init/rw
udev 10M 88K 10M 1% /dev
tmpfs 78M 0 78M 0% /dev/shm
/dev/sda1 137M 17M 114M 13% /boot
/dev/mapper/fileserver-backup
5.0G 144K 5.0G 1% /var/backup
/dev/mapper/fileserver-media
1.0G 33M 992M 4% /var/media
/dev/mapper/fileserver-share
50G 180M 47G 1% /var/share